DDoS attacks usually come out of nowhere and can bring in enormous amount of damage, many sites are very vulnerable, as they aren’t prepared to deal with this kind of situation. In recent years, number of DDoS attacks are growing, targeting all type of sites from small, private to corporative level. We are going to show you essential steps to detect, stop onginig DDoS attack on a site.
Also In this article we discuss quickly about DDos attack types, TCP transfer stack, monitoring, Linux, cover some administration tasks.
Setup:
Web server running on Ubuntu 18.04, 20.04, 22.04, LAMP stack, netstat, iptable
What is DDoS attack?
Amount of actions which aims to make a server unavailable to legitimate traffic by consuming all available server resources (transport/processing) causing the targeted device to not respond to a legitimate traffic at all or with big delay. (See header image)
Types of DDoS Attack can be different, a list of some common types: HTTP flood (GET, POST), Protocol attacks, SYN flood, reflected / spoofed attack.
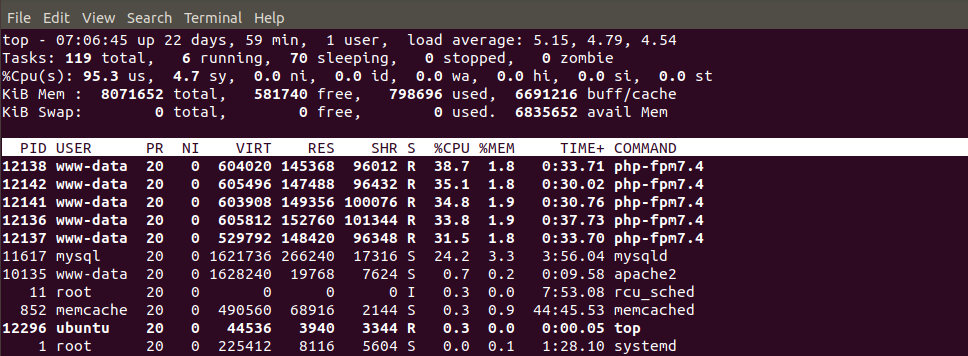
How to identify DDoS attack
The first sign of DDoS attack - site becoming unavailable, slow, high CPU load, spike in a traffic. Traffic analytics and monitoring tools can help you spot those signs:
- Suspicious amounts of traffic coming from a single IP address or IP range or one region.
- One type of device, web browser.
- Similar GET requests.
Linux command "netstat" used to detect incoming connections
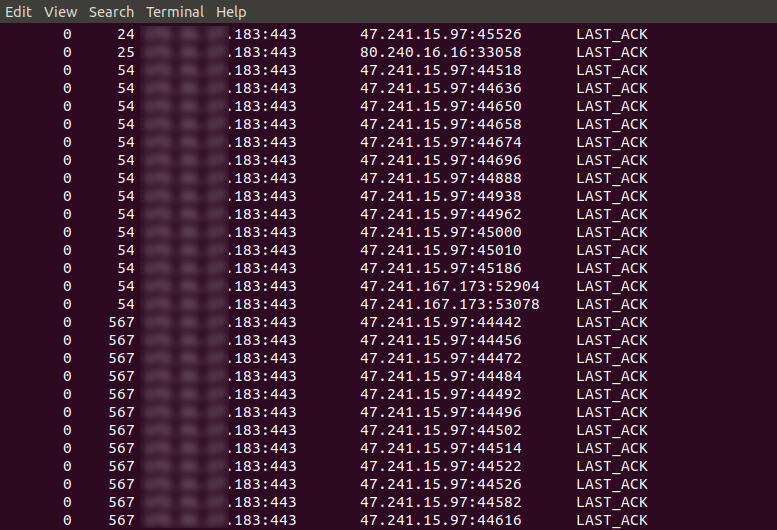
As we can see the results of "netstat" command, can be easy identified the source of an attack, in our case, it's IP 47.241.15.97 and 47.241.167.163, from those IP's incoming multiple connections attempts that are stuck in 3 way handshake (TCP) with stage LAST_ACK
How can DDos Attack be mitigated?
We will use a simple IP blocking by a single source or range as our attack has one source vector (incoming fake traffic source). When a Dos Attack is simple, this approach will be effective.
iptables -A INPUT -s 47.241.167.163 -j DROP
Linux command "iptables" used to block incoming connections from specified sources
Conclusion
Mitigating/stopping DDos attacks are complex, and require complex solutions. At almost all cases, mitigating attacks are require manual actions by specialists, this makes things complicated for small teams or site owners who don't have such specialists in dispose, leaving sites offline for a long time. With this article, it's easy to stop/mitigate DDos Attack. Good luck.
