Intro
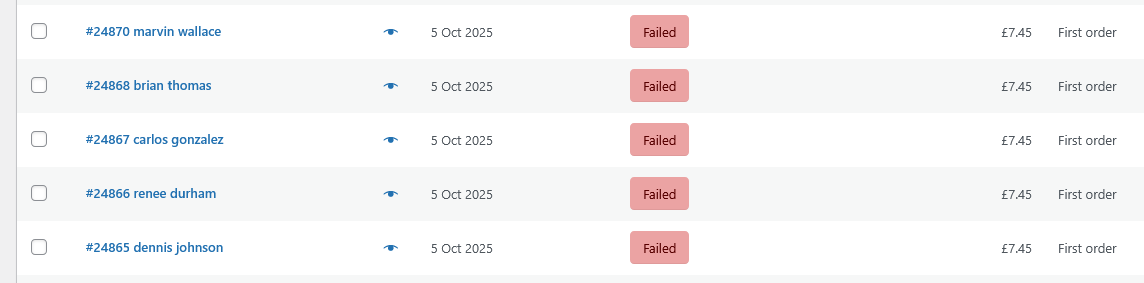
Every WooCommerce store owner dreads the sight of their orders dashboard filling up with hundreds of fake purchases. These are often the tell-tale signs of a bot attack or, more critically, a credit card testing scam, where fraudsters use your site to validate stolen credit card numbers.
Not only do these fraudulent orders clog your system and waste your time, but they can also lead to significant problems like unexpected payment gateway fees, damage to your sender reputation from excessive failed payment emails, and even account suspension.
If your WordPress and WooCommerce setup is under fire, and traditional CAPTCHAs aren't cutting it, you need a more robust defense. In this article, we will explain the mechanics behind these card testing scams—especially how they bypass common security measures—and provide you with several effective, technical strategies to permanently block bot traffic and safeguard your checkout process from this costly form of fraud.
What is a Card Testing Attack?
A Card Testing Attack is a type of fraud where criminals use automated scripts (bots) to run a large volume of stolen credit card numbers through an online merchant's payment processor using small-value transactions. The goal is to see which cards are valid and active so they can then be used for larger fraudulent purchases or sold on the dark web for a higher price.
What is a WooCommerce Bot spam Orders?
WooCommerce Bot Spam Orders are fake or fraudulent purchase attempts made on a WooCommerce-powered online store, typically by automated bots.
Analyzing and Tracing the Bot Attack
Step 1: Check Spam Bot Activity in Logs to Find the Fingerprint
Since surface-level details (IP, email) were easily rotated, the focus shifted to the raw server access logs to find a deeper, technical fingerprint.
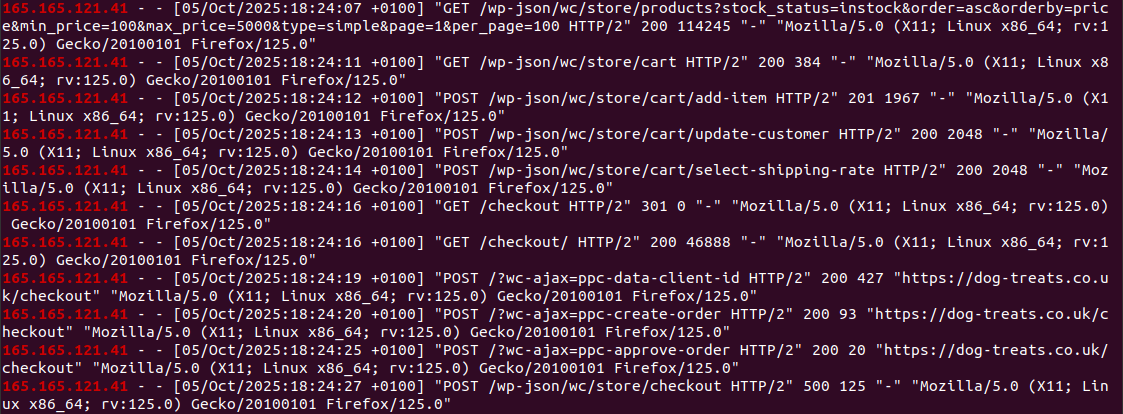
The logs consistently show the bots making requests to endpoints associated with the modern WooCommerce system, effectively bypassing any front-end security like CAPTCHAs.
Step 2: Identify the Exploited WordPress/WooCommerce Feature
The detailed log analysis confirmed that the bot attack was not running through the standard browser experience but was directly hitting the WooCommerce REST API endpoint used for checkout:
The bot was exploiting the /wp-json/wc/store/checkout or similar Store API endpoints. This is the feature that allows headless or block-based checkouts to function by accepting data via API without needing to render the traditional WordPress checkout page.
Because the traditional checkout protection (like CAPTCHA plugins) is only triggered by the visual page load, the bots were able to bypass all standard security by sending data straight to the API endpoint.
Analyzing the raw access logs clearly reveals that the spam bot activity is being carried out by making direct, high-volume requests to the Wordpress WooCommerce WP-JSON REST API endpoint.
Solution
The quickest and most effective solution is to disable or restrict access to the Wordpress WooCommerce WP-JSON REST API checkout endpoint (/wp-json/wc/store/checkout) via a small code snippet in your theme's functions.php file or a custom security plugin.
Summary
This guide illustrates that sophisticated bot attacks, like card testing or spam orders quickly evade superficial security measures such as blocking IP addresses or email domains. The key takeaway is the need for deep log analysis to identify the attacker's true vector—often a direct exploit of the Wordpress WooCommerce WP-JSON REST API endpoint—requiring advanced defenses like code-based endpoint restrictions.
